How o apply for an E2 automation
What is E2 Automation
Besides submitting reports using either the online web forms or the offline PDF forms, an organisation may also choose to submit their reports directly from their legacy SMS system. Many SMS providers include functionality to interface with external applications such as E2, allowing reports to be transmitted automatically without requiring manual re-entry.
What is an M2M user?
A “machine-to-machine” (M2M) user is basically a "device". In automated communication, M2M devices are designed to communicate with each other autonomously, without requiring human input. They can send and receive data or instructions to perform tasks, monitor conditions, or exchange information with other devices. An M2M user in Eccairs2, will use the exposed API methods allowing to perform tasks related to Submitting reports.
Types of automation
In general, there are two types of automation
· The SMS provider interfaces directly with E2 using the API methods. They create the reports using the exposed API methods
· The SMS provider interfaces with E2 by submitting reports in the E5X-format
Regardless how the SMS provider interfaces with E2, the following stages are common.
Stages
Submitting reports by an organisation is done in 3 stages
1. The sandbox stage
This stage is a purely technical IT step, designed to demonstrate that the organisation or its software provider is capable of connecting to E2 and transmitting reports via the API method.
· Objective: Prove technical connectivity and ability to submit reports through the API.
· Support: The E2 Support Team provides sufficient assistance to ensure that the organisation or SMS provider can establish a connection and successfully send reports.
· Report quality: At this stage, the content, quality, or completeness of the reports is not evaluated—only the technical submission process matters.
· Involvement: The Authority is not involved. Only the SMS provider and the E2 Support Team participate.
· Duration: If a software provider already has a proven record of connecting to E2 and submitting reports, this stage may be significantly shortened or even skipped.
2. The UAT stage
Once an organisation or its software provider is able to successfully send reports via the API interface in the Sandbox environment, access will be granted to the UAT (User Acceptance Testing) environment.
· E2 Support will notify the SMS provider to contact the relevant Authority to which the organisation reports.
· The organisation, either using its own system or software supplied by the SMS provider, will submit reports through this environment.
This UAT stage continues until the Authority confirms successful validation and gives the official green light for production.
3. The production stage
The is the last stage, connecting and sending reports to E2 using the API should be flowless and the quality should be of high enough quality.
URLs
· PROD --> https://api.aviationreporting.eu
· UAT --> https://api.uat.aviationreporting.eu
· SANDBOX --> https://api.sandbox.aviationreporting.eu
What data is to be provided?
· Stage 1 (Sandbox)
The name, first name and email address of the focal point at the organisation dealing with technical issues
The IP addresses of the organisation servers from which the API will be invoked
(format 111.222.333.444/xy)
· Stage 2 (UAT)
The name, first name and email address of the focal point at the organisation dealing with submitting test reports
· Stage 3 (Production)
Same as stage 2
What will the E2 Support Team do?
· Setup the Sandbox
· Provide technical assistance in stage 1
What is the Authority to do?
· Setup the UAT and Production environments
· Validate the submitted test reports in UAT
· Give feed back to the organisation
· Give the green light to go to production
Setting Up an M2M user
What permissions does a user need to have?
Before a user can setup a M2M user, a dedicated role (M2M CRUD) is to be assigned to him. It is the E2 Support Team that will add this permission to the National Security Administrator. This will be done for the first time that an M2M user is to be created in one of the Authority’s organisations.
How to access the M2M creation?
Depending on the user’s permissions, the Organisation management can be opened
As a M2M user can only exist in an existing Organisation, the organisation is to be opened in detail
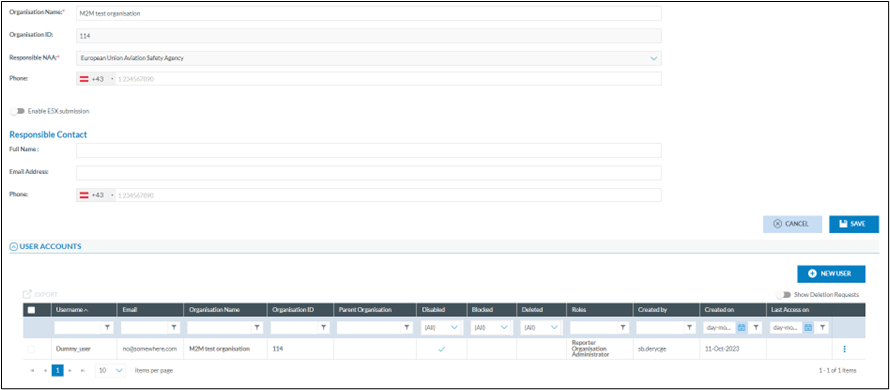
How to add the M2M user to the organisation?
Although a Machine-to-Machine (M2M) user is not the same as a human user, it is created in the same way.
1. Click on the “New User” button – the User Creation window will open.
2. Select the M2M tab – this will open the M2M User Creation window.
3. If the M2M tab is not visible, it means that the user attempting to create the M2M account does not have the required M2M CRUD role.
Assigning the M2M CRUD Role:
· The first time, this role is assigned by the E2 Support Team.
· Afterwards, it is managed by the Authority’s national security administrator.
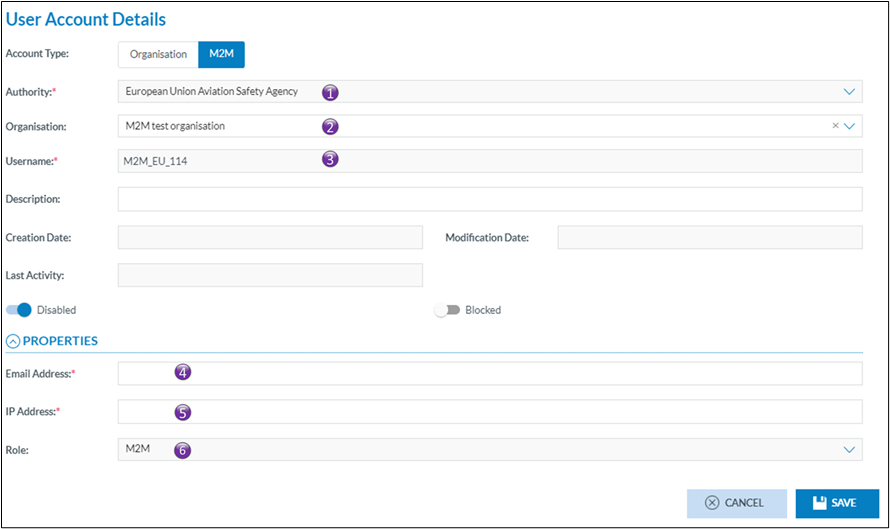
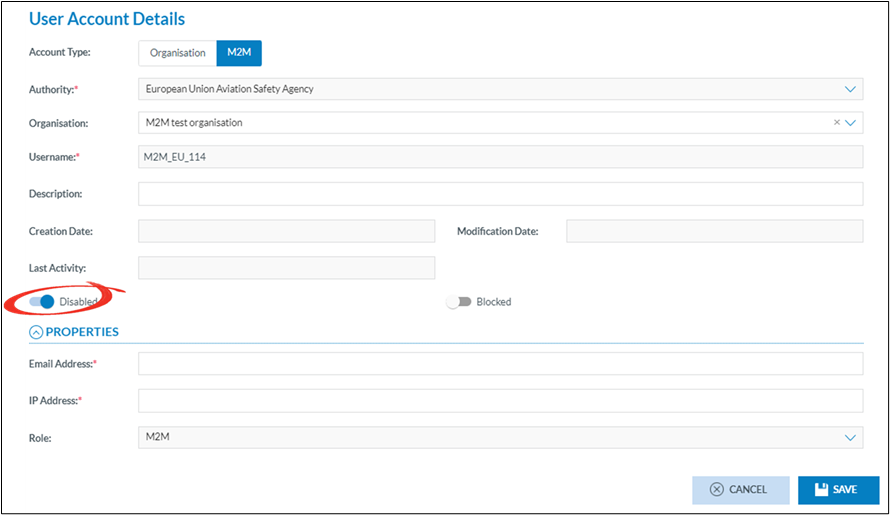
1. Is the name of the Authority in which the M2M user is created. This is prefilled and cannot be modified. It is the Authority of the user that creates the M2M user
2. Is the name of the organisation in which the M2M is to be created
3. Is the username, the username is automatically generated by the system. It ensures that the username is unique throughout Eccairs2. As this is an automatically assigned username, that means, when creating a M2M user for the same organisation in another environment it will not be the same
4. Is the email address to where the activation email for the M2M will be sent. Often this is the email address of the person responsible for the M2M interfacing
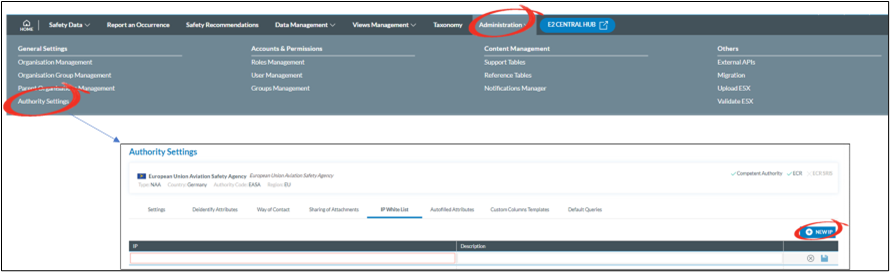
5. Before access to E2 is allowed via a M2M interface, E2 is to know the IP-address(es) of the machine(s) with whom it will communicate. Here only one IP address can be added. If more than one IP address is to be added, then this is to be done via the Authority settings.
6. The role assigned to the M2M user, this is Automatically done by the system and cannot be changed. If this is empty, then a configuration error has occurred, and it is key to create a service desk ticket.
Frequently asked questions
How many M2M user can an organisation have?
Only one M2M is allowed per organisation. The access to E2 is given via the whitelisted IP addresses so no need for extra M2M users
Who will activate the account?
As with all accounts, an activation email will be sent to the email address mentioned in the M2M user’s profile (4). The activation email will be valid for 6 hours
What to do if a M2M activation code has expired?
In the event an M2M activation code expired (> 72 hours), the M2M user can no longer be activated by the user. The activation code can be resent following these steps
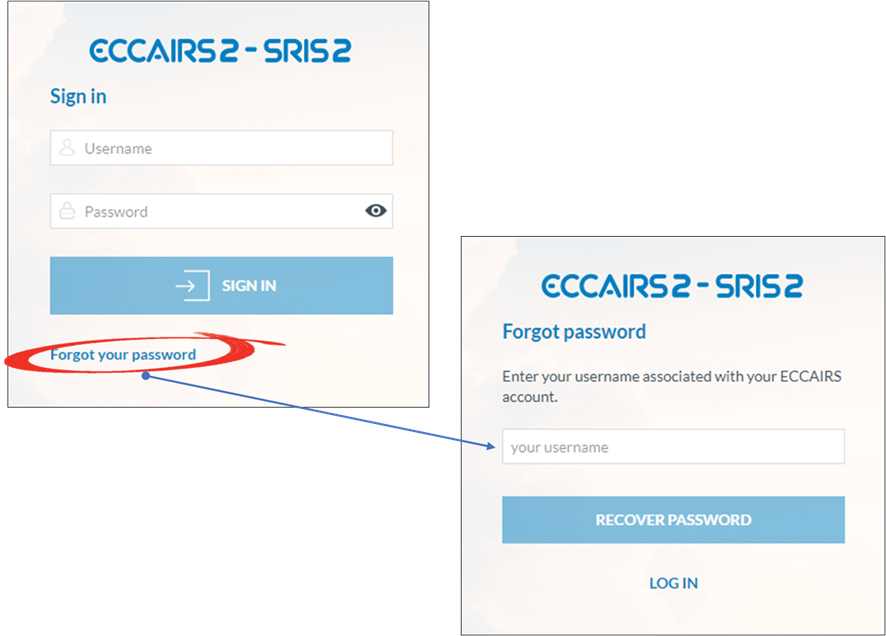
1. Enable the M2M Account
2. Open the ECCAIRS logon screen and click forgot password
An email will be sent to the email address linked to the username, which is not necessarily the same as the user resending the activation email
What if the email address of the M2M user changed?
Like with all other accounts, email addresses can easily be modified.